This one small step by the government can be a giant step in boosting the cybersecurity of millions
As part of its Digital India initiative, the central government has been readying its cyber warfare arsenal. Its latest weapon is a mobile and desktop security solution that will notify, enable cleaning and secure devices and systems of end-users.
The Ministry of Electronics and Information Technology (MeitY) launched this solution — a botnet cleaning and malware analysis centre called the Cyber Swachhta Kendra 1 through CERT-IN 2 recently. The Kendra provides information and tools to users to secure their systems and devices.
This is an important move by the government to protect citizens from cyber attacks. But it needs to take another step — something that it has not done effectively so far — to actually secure mobile and desktop security of the millions of Indians using government websites. And it’s a pretty simple step at that. All it has to do it buy valid SSL certificates for all its web applications.
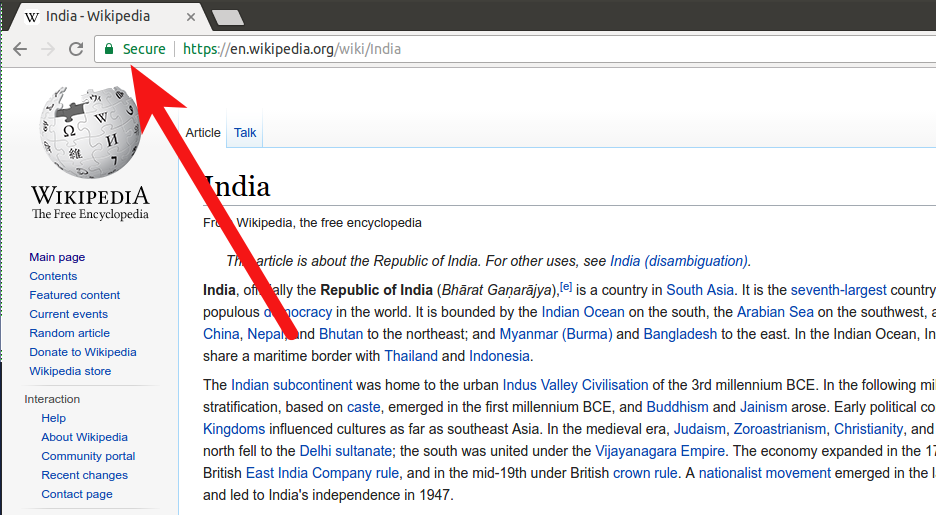
SSL (it stands for secure sockets layer) or https is part of a set of technologies which makes communication between a consumer and web service provider private and safe. You can instantly recognise it when you visit an eCommerce website or Wikipedia as you will see a green lock to the left of the URL bar. This green lock signifies that you are visiting the authentic Wikipedia and all the communication between you and Wikipedia is private.
Now anyone can create an SSL certificate, but browsers don’t trust them to be authentic until it is countersigned by a trustworthy middleman. The job of the middleman is to validate that SSL certificate is actually owned by the owner of the URL and sign it to confirm the same. Since browsers trust this middleman, they will trust the certificate and show the green lock.
There are thousands of such middlemen which browsers trust. One such signatory was the National Informatics Centre (NIC), which signed some SSLs related to government websites. The NIC derives its power from Indian Controller of Certifying Authorities (IndiaCCA). However, in july 2014, the NIC was caught issuing unauthorised digital certificates for several Google domains. After investigation, IndiaCCA revoked the NIC’s rights and all the certificates signed by it became untrustworthy. But at the root, IndiaCCA is responsible for all the certificates issued under its authority. So Chrome removed trust from IndiaCCA, followed by other browsers. This made thousands of websites untrustworthy as they were using a certificate signed by one of the licensed certifying authorities.
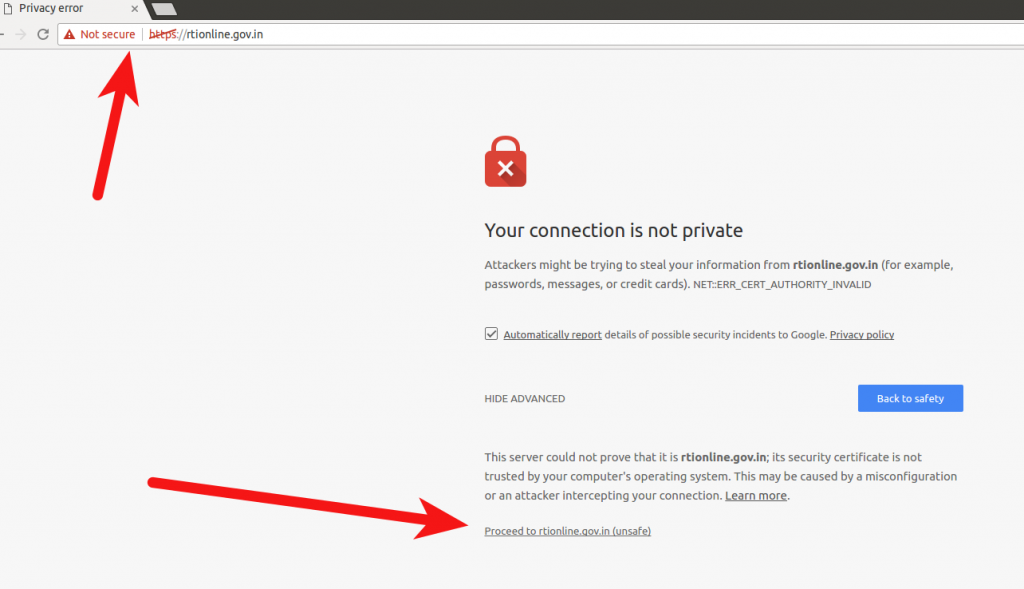
Even in 2017, there are government-run websites like https://rtionline.gov.in/ a portal to file RTI application and appeals online along with payments using the certificate signed by (n)Code which come under IndiaCCA. If a user visits the RTI website, she will be shown a scary message which she has to to bypass manually.
You may wonder what’s the big deal if users can bypass the page simply by clicking a link. Well, it’s easy to bypass the error page, but it sets a wrong precedent. Most regular users wouldn’t know what the error is and won’t be able differentiate between an error like this and an attacker intercepting the connection to steal information. So, it is not advisable to prescribe users to skip an error or add an exception, especially at a time when the government is urging Indians to conduct financial transactions online.
It’s high time that government bought SSL certificates from other vendors to safeguard its websites to enable users to access the sites without violating security best practices. This small step will go a long way in increasing the security of millions of Indians.
This post first appeared on FactorDaily as This one small step by the government can be a giant step in boosting the cybersecurity of millions. Edited by Prakriti.
Footnotes:
- While writing this article I wanted to link to the HTTPS version of Cyber Swachhta Kendra website — https://www.cyberswachhtakendra.gov.in — which started throwing an SSL error for completely different reason — a Certificate name mismatch. The Cyber Swachhta Kendra has advice and best practices for common users to follow. But, it doesn’t seem to be following the minimum best practices for websites and is putting its users at risk.
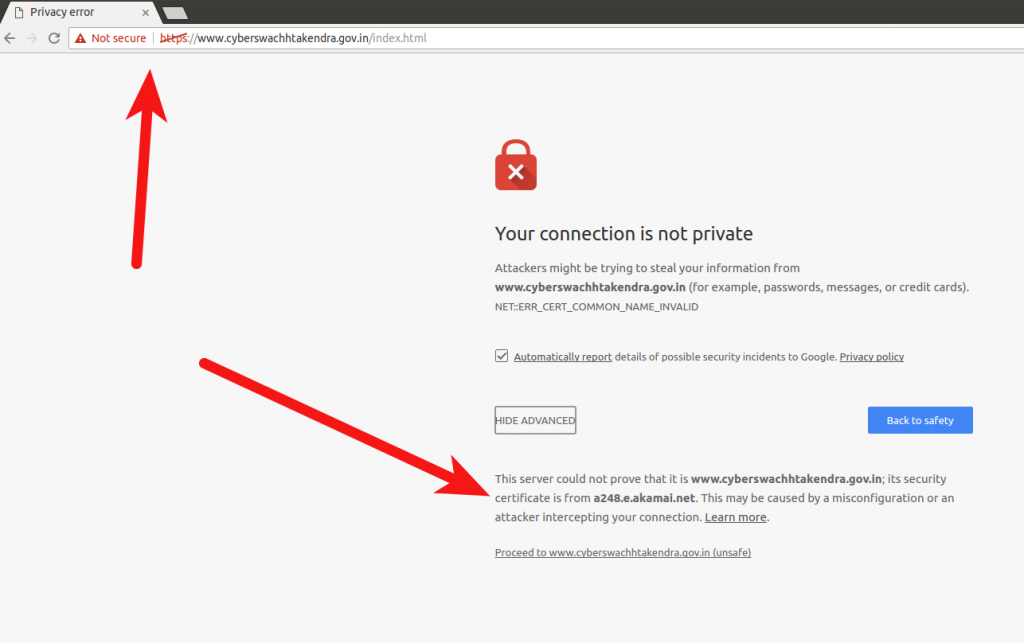 ↩
↩ - CERT-IN, the national nodal agency tasked with dealing with cybersecurity threats in India, doesn’t seem to have a secured version of its website https://www.cert-in.org.in. This shows how CERT-IN too doesn’t follow the minimum best practices for websites, leaving users vulnerable to cyberthreats. ↩