India urgently needs responsible disclosure policy guidelines for vulnerability reporting
This year has been an interesting one for infosecurity in India. Major infrastructure services — from identity to payment services — have gone online. This is also the reason why there is a lot of conversation happening around general and operational security. But what’s lacking is talk around missing guidelines to report security issues in India.
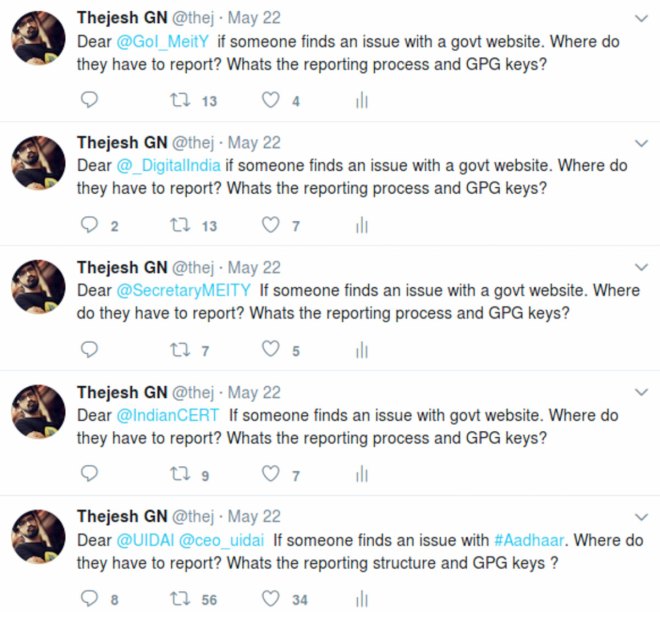
In the absence any public guidelines or discussions, I tweeted to major infrastructure providers and institutions responsible for cybersecurity like @IndianCert, @NCPI_NCPI, @UPI_NCPI, @GoI_MeiTY,@_DigialIndia, @SecretaryMEITY, @UIDAI, etc, asking them for the process of reporting vulnerabilities and a secure way of contacting them. None of them replied, except for @UIDAI, and its reply seemed like a standard social media message, asking me to send the query through Twitter direct message. Institutions like India CERT have a mandate to provide a single-point contact for reporting and be available 24×7. But they are unresponsive and don’t have any guidelines for the reporters.
The National Critical Information Infrastructure Protection Centre (NCIIPC) was created by the Government of India with a mission “To take all necessary measures to facilitate protection of Critical Information Infrastructure, from unauthorised access, modification, use, disclosure, disruption, incapacitation or distraction through coherent coordination, synergy and raising information security awareness among all stakeholders.”
The NCIIPC is responsible only for critical infrastructure, and not for any public or private organisation. Even though it has PDF forms to report vulnerabilities or incidents, it’s targeted towards vendors and not towards ethical hackers or security researchers. They also don’t have a publicly available policy which defines what process will be followed after reporting or what kind of legal protections are provided to security researchers.
It’s not to say none of the Indian organisations have a policy. There are private organizations like Zomato, FlipKart, etc, which do have policies for reporting security vulnerabilities. But most public institutions don’t have processes or policies in place for handling responsible disclosure. They need guidelines that they can use to set up such a process and policy to communicate with stakeholders.
Most public institutions don’t have processes or policies in place for handling responsible disclosure. They need guidelines that they can use to set up such a process and policy to communicate with stakeholders.Without policies, reporting is difficult and response from system owners is unpredictable. If you take some recent cases in India, vulnerability reporters need to go through loops to reach system owners because there is no standard way of reaching them like in the case of the UIDAI. Sometimes, even if you reach the system owners, vulnerabilities don’t get fixed properly, like in the case of Narendra Modi’s website, and hence the problems reappear in another form. In several cases, system owners don’t even care about security issues, or worse, they go after researchers for disclosing vulnerabilities instead of fixing the issue.
What’s responsible disclosure policy guidelines?
Wikipedia has a very concise definition of “responsible disclosure”: “Responsible disclosure is a computer security term describing a vulnerability disclosure model. It is like full disclosure, with the addition that all stakeholders agree to allow a period of time for the vulnerability to be patched before publishing the details.”
A responsible disclosure policy defines the process for the stakeholders to communicate with each other, fix the issue and communicate to a larger public. It defines the responsibilities of each stakeholder, how the disclosures are handled, what are the timelines, the communication process, legal protection, rewards if any, what’s allowed and not allowed, etc.
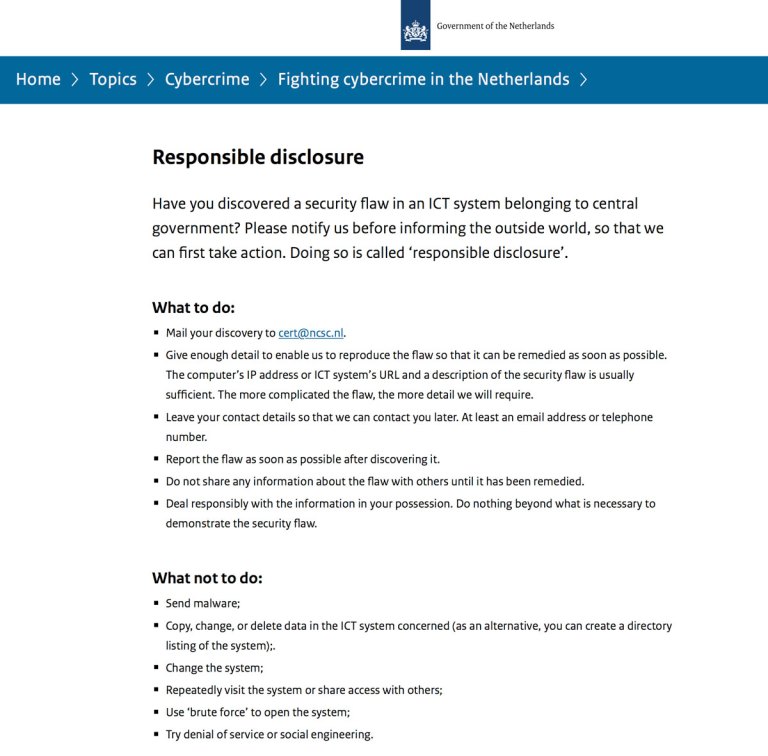
Responsible disclosure policy guidelines are the framework that organizations can use to come up with their own policy, based on their setup, resources, importance etc.In 2013, the Netherlands was one of the first government to come up with a Responsible Disclosure Guidelines. It’s hailed as one of the best. It’s a framework that can be used by any private or government institution in the Netherlands to draft their own Responsible Disclosure Policy. There is even a template that organizations can use to create their policy.
And for India?
Its high time that the NCIIPC, CERT and MEity come together with other stakeholders to draft responsible disclosure policy guidelines for India. This will help a lot of government and private organisations to come up with their own policies. It will also encourage individual security researchers report incidents or vulnerabilities and help to strengthen the digital infrastructure of India.
This post first appeared on FactorDaily as India urgently needs responsible disclosure policy guidelines for security reporting. Edited by Prakriti.










1 Response
[…] allows for the state to pen-test IoT devices operating in the country to identify weaknesses. In India, calls have long been made for the government to release public vulnerability reporting guidelines. And while no vulnerability […]