How to stay anonymous online
I like to use my real name everywhere. But I can afford to that because I am in a reasonably safe place. But there are people who rationally fear retaliation from employers, bad police, bullies, or the rogue state. So it makes sense to stay anonymous.
It is very difficult to stay anonymous online. I believe there is no way you can remain anonymous forever. Finding you depends on how much time, intelligence, computer power and motivation your opponents have. Identification can only be delayed for practically long time depending on the steps you take.
This how-to is not probably complete. My knowledge is quite limited. But if I ever want to remain anonymous, I would follow all of them. In fact I follow most of these steps just to be safe online.
I have tried to make it as simple as possible for non techies. But there are pointers for the geeks to follow into the rabbit hole. They are usually marked with [g] for geek alert.
Trustable Fake Identity
There are two ways to remain anonymous online. Say if you are a blogger, your username could be so obvious that your adversaries will know you are trying to hide or you could use a very realistic fake identity which will confuse them. I would go second way. But I would give a thought about country, city, religion, sex and other identifiable characteristics of my identity before I decide on upon one. It's very important to create a trustable fake identity. It's not an easy job. So work on it.
Computer OS - Linux
The most important thing to remain safe online is to keep your computer safe. You need to be able to trust your computer to do the right thing.  I use Linux (Debian/Ubuntu). I trust them because its open source and most of the vulnerabilities are available in the public domain. So I know whats going on in the system.
I use Linux (Debian/Ubuntu). I trust them because its open source and most of the vulnerabilities are available in the public domain. So I know whats going on in the system.
So use Linux as much as possible. If you can't avoid using Windows or Mac try dual booting or a live CD. Linux like before is not very difficult to use these days. Distros like Ubuntu are very user-friendly. Try it.
Tails is a live CD or live USB that aims at preserving your privacy and anonymity. It helps you to use the Internet anonymously almost anywhere you go and on any computer. All connections to the Internet are forced to go through the Tor network. The OS leaves no trace on the computer you're using unless you ask it explicitly. It uses state-of-the-art cryptographic tools to encrypt your files, email and instant messaging. It's an all in one package which is very useful non geeks. Install it on your USB and use it.
For highly paranoid ones there are distros like TinFoilHat [g] available. It even protects you against electromagnetic radiation eavesdropping [g].
Disk Encryption
Have you ever thought what happens to your data if you lose your machine or give it for repair? Remember your data is your identity. Its very important to encrypt your hard disk. On Ubuntu you can enable home directory encryption by default. In case if you find it difficult or you have many portable harddisks or use any other OS then use TrueCrypt. It's an open-source, transparent, on the fly encryption which is very easy to use. It works on all the platforms. Portable versions are available too.
Firewall and Anti virus
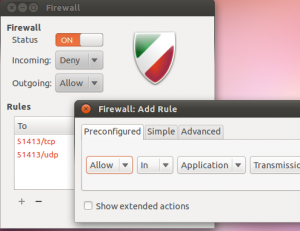 Keeping your computer safe is very important to anonymous online. You really don't want a trojan horse sending your information to somebody. Ubuntu comes with built-in firewall (it's not difficult to install one either). You can install Gufw which is a great GUI to support your Ubuntu firewall. Latest version of windows comes with the firewall. Enable it if you haven't already.
Keeping your computer safe is very important to anonymous online. You really don't want a trojan horse sending your information to somebody. Ubuntu comes with built-in firewall (it's not difficult to install one either). You can install Gufw which is a great GUI to support your Ubuntu firewall. Latest version of windows comes with the firewall. Enable it if you haven't already.
Anti virus is a necessary evil. I use Avast and clamav. Both are available for all three platforms. clamav is an open source project. I prefer using it.
Connecting to Internet - Tor
On internet every machine will have an ip address. It works as a primary identifier online. It's very important to hide/fake it to remain anonymous. Tor is free software and an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis. Individuals, journalists, whistle blowers from all over the world use Tor. You should use it too.
 Tor prevents anyone from knowing your location or browsing. Tor can be used with browsers, instant messaging clients, remote logins, and more. Tor is free and open source for Windows, Mac, Linux/Unix, and Android phones. You should use it.
Tor prevents anyone from knowing your location or browsing. Tor can be used with browsers, instant messaging clients, remote logins, and more. Tor is free and open source for Windows, Mac, Linux/Unix, and Android phones. You should use it.
Tor Browser Bundle[g] lets you use Tor on Windows, Mac OS X, or Linux without needing to install any software. It can run off a USB flash drive, comes with a pre-configured web browser to protect your anonymity, and is self-contained. Very useful when you are traveling and want to remain anonymous.
Tor makes your traffic is channelized anonymously but it doesn't promise data security between you and the end server. You must always use HTTPS, encrypt your mails, OTR for IM etc.
[g] Active content, such as Java, Javascript, Adobe Flash, Adobe Shockwave, QuickTime, RealAudio, ActiveX controls, and VBScript, are binary applications. These binary applications run as your user account with your permissions in your operating system. They might bypass Tor. I would avoid using them when I want to remain anonymous.
Special case : Open Public WiFi
Public WiFis (or any wifi/lan which you not in control of) are not safe. Don't fall for free wifi at coffee shops or at any other public spaces if your concern is privacy and safety. Data between your computer and wifi router is plain text and anybody on network can read it. As though you are reading your dairy loud and clear. If you really want to use public wifi, you must use https at the least.
[g] I have a machine at home which runs Tor and acts as VPN server for me. On public Wifi I connect through my home VPN server which goes through Tor. My setup is similar to the one explained in this blog title Tor on SSH. It's not very difficult to build an SSH tunnel yourself.
[g] SSHing over Tor is very interesting.
Browser - Firefox
I will use Firefox since it's the best Free and Open Source software available. Keep updating it. Use private browsing mode.
Browser Add Ons
Https Everywhere Many sites on the web offer some limited support for encryption over HTTPS, but make it difficult to use. For instance, they may default to unencrypted HTTP, or fill encrypted pages with links that go back to the unencrypted site. The HTTPS Everywhere extension fixes these problems by rewriting all requests to these sites to HTTPS.
No Script Blocks Javascript. The best security you can get in a web browser!
Allow active content to run only from sites you trust, and protect yourself against XSS and Clickjacking attacks.
Tor Button Torbutton is the component in Tor Browser Bundle that takes care of application-level security and privacy concerns in Firefox. To keep you safe, Torbutton disables many types of active content.
Better Privacy serves to protect against special longterm cookies, a new generation of 'Super-Cookie', which silently conquered the Internet. This new cookie generation offers unlimited user tracking to industry and market research. Concerning privacy Flash-cookies are most critical.
This add-on was made to make users aware of those hidden, never expiring objects and to offer an easier way to view and to manage them - since browsers are unable to do that for you.
Special case Browser plug-ins
Active content, such as Java, Javascript, Adobe Flash, Adobe Shockwave, QuickTime, RealAudio, Silverlight, ActiveX controls, VBScript, etc are binary applications. They run inside a sandbox in the browser. They aren't safe. Disable them if you don't want.
Email- Encryption - GPG
 If you are online you have to use email. Use a provider who gives HTTPS access to email. Keep it in sync with your fake identity. Use it only for the related communications and nothing else. It's very important to keep it safe. But remember just the HTTPS doesn't promise security. You need to encrypt it. Get used to GPG encryption if you want complete privacy. It's not very difficult. You can GPG-Shell which is great UI for GPG or GPG4USB which is a simple and clean UI that can be used by anybody. Try it.
If you are online you have to use email. Use a provider who gives HTTPS access to email. Keep it in sync with your fake identity. Use it only for the related communications and nothing else. It's very important to keep it safe. But remember just the HTTPS doesn't promise security. You need to encrypt it. Get used to GPG encryption if you want complete privacy. It's not very difficult. You can GPG-Shell which is great UI for GPG or GPG4USB which is a simple and clean UI that can be used by anybody. Try it.
GPG is a must if you want to keep your communications secure. Make sure the keysize is at least 2048 bits.
[g] You can also use GPG with RetroShare is an Open Source cross-platform, private and secure decentralised communication platform. It lets you to securely chat and share files with your friends and family, using a web-of-trust to authenticate peers and OpenSSL to encrypt all communication. RetroShare provides filesharing, chat, messages, forums and channels. I USE IT.
IM - OTR
If you like to use your regualr IM and keep the conversations off the record. This off the record is not same as GChat OTR. Gchat OTR is lame. It's not actually OTR. You should use OTR Plugin with pidgin and google IM account for this. Installation is quite easy.
[g]Off-the-Record (OTR) Messaging allows you to have private conversations over instant messaging by providing Encryption (No one else can read your instant messages.), Authentication (You are assured the correspondent is who you think it is.) Deniability (The messages you send do not have digital signatures that are checkable by a third-party. Anyone can forge messages after a conversation to make them look like they came from you. However, during a conversation, your correspondent is assured the messages he sees are authentic and unmodified.) Perfect forward secrecy (If you lose control of your private keys, no previous conversation is compromised.)
Blogging
Use the fake identity and email. Avoid using any Javascript or flash embedded content as much as possible. Specially avoid Advt and analytic. Have a very strong password.
[g]if you are paronoid it's not difficult to sign your blog post. Just to avoid hostile take over your blog account and posting on your blog on your behalf.
Posting pictures or videos
When you are posting picture and videos online remove the metadata. Some cameras and phones are known to leave signatures on them. Be careful about it. Make sure people who appear in the picture/video are okay with it and sworn to confidentiality of your identity. Or you might have to mask them with really good software (lame work can lead to reconstruction of the image, identification of them and then you). Like ObscuraCam for Android camera.
Passwords and reset password settings
Make sure your passwords are strong and long. Specially of your email. Once somebody gets access to your email then he gets access to all your accounts. So it's very very important. Also make sure reset password(or forgot password) questionnaires of all your accounts are strong.
End Note
I have wanted to share this for a long time. But then its #MakeBlog which got me to write this. Thanks guys.
Obligatory warning: Use it to protect yourself and not to harm anybody. This article is written as per my best knowledge. There could be loopholes. Let me know if you find any. I will buy you a coffee, update the post and give credit.
You can use my GPG public keys to send an encrypted email.









Deliciously paranoid. Love it. After all, you aren’t paranoid if they are really out to kill you…
Wanted to add behavioral suggestions – non-tech – if they are useful:
Nothing beats the capacity of the human brain to encrypt. For really sensitive stuff, set up and use codes. For example, call a mafia don a baby, a smuggling ring the kindergarten, a specific meeting time as lunch, name locations 1km to the south of where you mean (or worse – add distance, and displace in degrees or use the name of the nearest wine shop or school instead of locality…), different gun brands as fruit names… and have a party talking about that kid in the kindergarten eating five kinds of jam at lunch. Done well, you’ll be dead of old age and decomposed before they crack it. This is also useful beyond internet – phones for example are simple and cops monitor at will.
AND
Disinform. If using fake profile (or real), use contradictory data. One day you’re 27, living in Calcutta, another day, you’re a transgender living in New York, vegetable vendor in China… you can get just as accurately profiled under a fake name as real. If a point is being monitored, rather than you specifically, IDing you should be hard work.
Do NOT use social networks. If you must, obscure ones requiring login are better than something like facebook or twitter. If you must use one where another has an account, twitter is marginally safer. Facebook will track your last sneeze AND unhesitatingly provide it in excruciating detail to cops if legally requested.
To delete content off the net:
Caches and stuff hold on to versions of your pages for ages. There are pages years old cached and used as replacement links for original. That bad. So if you want to get a critical page out, what do you do? Edit it. Remove sensitive content, save. Let caches update (if necessary, alert a search engine about an already indexed page). Lather, rinse, repeat a couple of times, but chances are one edit will lead to updated caches within days. Then file for removal requests if you want, and let it take its own sweet time.
Had a list, will try and find. Some may be more or less useful. So evaluate with advice from one who knows thoroughly.
The above examples assume you are working for the powers of good and whistle blowing a mafia-police nexus.
The reason for the fake data, as I understood it is that your data collected doesn’t mean shit if the bot can’t make sense of it, and it is too voluminous and complex to decode manually. In other words, it eats their cheap storage space, but for all practical purposes might as well not exist.
Sensitive emails, don’t send. Write draft, share password (which can also be incremented in a predetermined way). Let the other read, delete, rewrite draft as reply to you. Lather, rinse, repeat. No copies in trash, no trace of what was deleted, no splatter of records on servers. A general theme is that what is deleted can be recovered, what is edited gets updated to the harmless version with no way of recovering earlier.
WordPress blogs can be used in a similar way. Edit an already written post. DON’T SAVE. Let the WordPress autosave do its magic. You will have a revision of the post stored in the database (which need not be the post at all, of course), but your post remains the published version as long as you DON’T UPDATE it yourself.
Of course, this will save a copy of what you wrote in an obscure place, so it isn’t as secure as the data vanishing, but hey, sometimes you need to store…
Thank You Thejesh and Vidyut.
Have you tried Freegate? I am not very sure on how much it helps protects privacy; but it definitely helps overcome “some great walls”!
VPN Services that allow payment with BTC or Liberty Reserve are also great ways to stay anonymous.
Agree. Started minting bitcoins :)
How to configure Tor, so that we can connect to the server what we really wanted i.e., If I want to connect to US channel in Tor – How to do that?
It seems like I live in big brother house. It seems like the police watch me. That has an up-side. :-) I seem to be blocked from real people on the Internet. The radio talks to me. I have nanosecond reflexes.
I gave-up being two faced with face-book. My parents spy on me.
The least likely thing is bodily harm. ROFLMAO. God’s just so if it happened, I’d deserve it or be blessed like St. Paul.
God says…
and they shall be utterly burned with fire in the same place.
23:8 These be the names of the mighty men whom David had: The
Tachmonite that sat in the seat, chief among the captains; the same
was Adino the Eznite: he lift up his spear against eight hundred, whom
he slew at one time.
23:9 And after him was Eleazar the son of Dodo the Ahohite, one of the
three mighty men with David, when they defied the Philistines that
were there gathered together to battle, and the men of Israel were
gone away: 23:10 He arose, and smote the Philistines until his hand
was weary, and his hand clave unto the sword: and the LORD wrought a
great victory that day; and the people returned after him only to
spoil.
This does not work, there is a way to assemble the pieces offline through a network of partnerships. Online privacy is nothing but a dream.
thank you for a good article.
I use encryption SSH tunnel and proxy solution with http://pirateray.com/proxy , it works with any browser on Windows and Linux, easy to install and free to try.
This solution changes real IP and encrypts the traffic, so your ISP cannot see what you are doing.
Hurrah! After all I got a weblog from where I can in fact obtain useful data regarding my
study and knowledge.
Thank you for some other informative web site.
Where else may just I am getting that kind of information written in such a perfect manner?
I’ve a venture that I am just now operating on, and I’ve been at the glance
out for such info.
Wow, incredible blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your site is magnificent, as well as the content!
wynajem kopiarek kserokopiarkiprofit.pl k$er0k0pi4rki
Heya i’m for the primary time here. I found this board and I to find It truly useful & it helped me out much. I am hoping to give one thing back and aid others such as you helped me.
Good article, thanks. I usualy take proxy from http://www.proxybridge.com/ and put it in my browser setings. Works great.
I appreciate for the information. I will book mark this blog.
Hello! I just wanted to ask if you ever have any problems with hackers?
My last blog (wordpress) was hacked and I ended up losing several weeks of hard work due to no back up.
Do you have any methods to prevent hackers?